Let's Encrypt!
I wanted to do https on my new website and started to look for free but trusted certificate authorities. When I found Let's Encrypt i knew it had to be this!
What is Let's Encrypt?
LE is a certificate authority (CA) which currently runs in public beta for automated TLS certificate enrollment. Users running web servers can easily create cron scripts to request & renew certificate for their websites. Totally automated and totally open & free!
Two Types: Webroot & Standalone
Standalone mode requests/renews a certificate. It starts it's own tiny webserver to do so listening on 80 and/or 443 to verify the legitimacy of the fqdn in the request. The problem with this mode is that a running webserver on 80 an/or 443 should be shutdown during this proces.
Webroot is a mode where a vhost is used to do the request and verification. The nice thing about this is your websites can keep running 24x7!
Currently only available for Apache, but other modules (like nginx) are being built.
I use nginx and using standalone mode (for now), on a weekly basis, so every week my site would be down for a few seconds or so.
How it works!
The basis you need to know how to set up a LE can be found here. But i'm going to make i even easier for you if you're running nginx (on a RPi like i do).
Get Let's Encrypt!
``` $ sudo apt-get update $ sudo apt-get -y install git bc $ sudo git clone https://github.com/letsencrypt/letsencrypt /opt/letsencrypt $ cd /opt/letsencrypt $ sudo ./letsencrypt-auto ``` #### DNS and availability webserver 1. You need a working DNS A record for your webserver! 2. You're webserver needs to be available on the internet on ports 80 and 443 #### Cron ``` root@web:/etc/cron.weekly# cat letsencrypt-renew-scict.nl.sh #!/bin/sh cd /opt/letsencrypt service nginx stop #./letsencrypt-auto certonly --standalone -d scict.nl -d www.scict.nl -d lebber.net -d www.lebber.net -d fotoboek.lebber.net --renew --rsa-key-size 4096 --keep-until-expiring ./letsencrypt-auto certonly --standalone -d scict.nl -d www.scict.nl -d lebber.net -d www.lebber.net -d fotoboek.lebber.net --rsa-key-size 4096 --keep-until-expiring service nginx start</font>
#### SSL Labs A+ score in nginx!
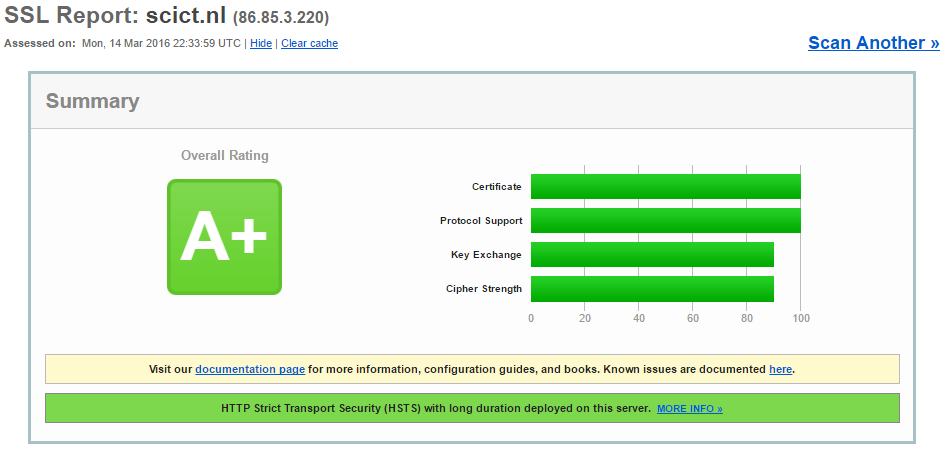
Links i used: [Mozilla](https://mozilla.github.io/server-side-tls/ssl-config-generator/)[^n] & [Michael Lustfield](https://michael.lustfield.net/nginx/getting-a-perfect-ssl-labs-score)[^n]
<font size=3>
root@web:/etc/nginx/sites-available# cat ghost-blog
server {
listen 80;
listen [::]:80;
server_name scict.nl www.scict.nl;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl;
gzip off;
server_name scict.nl www.scict.nl;
ssl_certificate /etc/letsencrypt/live/scict.nl/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/scict.nl/privkey.pem;
#ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
#ssl_prefer_server_ciphers on;
#ssl_ciphers 'EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH';
# https://mozilla.github.io/server-side-tls/ssl-config-generator/
# also read: https://michael.lustfield.net/nginx/getting-a-perfect-ssl-labs-score
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:50m;
ssl_session_tickets off;
# Diffie-Hellman parameter for DHE ciphersuites, recommended 4096 bits, 2048 is also fine, 4096 very slow on Pi, -dsaparam is faster.
# openssl dhparam -out /etc/nginx/ssl/dhparam.pem 4096 ran on i7 laptop
# openssl dhparam -out /etc/nginx/ssl/dhparam.pem 4096 -dsaparam on rpi2
ssl_dhparam /etc/nginx/ssl/dhparam.pem;
# modern configuration. tweak to your needs.
ssl_protocols TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECD HE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
#ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384';
ssl_prefer_server_ciphers on;
# HSTS (ngx_http_headers_module is required) (15768000 seconds = 6 months)
add_header Strict-Transport-Security max-age=15768000;
# OCSP Stapling ---
# fetch OCSP records from URL in ssl_certificate and cache them
ssl_stapling on;
ssl_stapling_verify on;
location / {
proxy_pass http://127.0.0.1:8002;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
}
}
</font>
[^n]: https://letsencrypt.org/getting-started/
[^n]: https://mozilla.github.io/server-side-tls/ssl-config-generator/
[^n]: https://michael.lustfield.net/nginx/getting-a-perfect-ssl-labs-score